Webhook Configurations
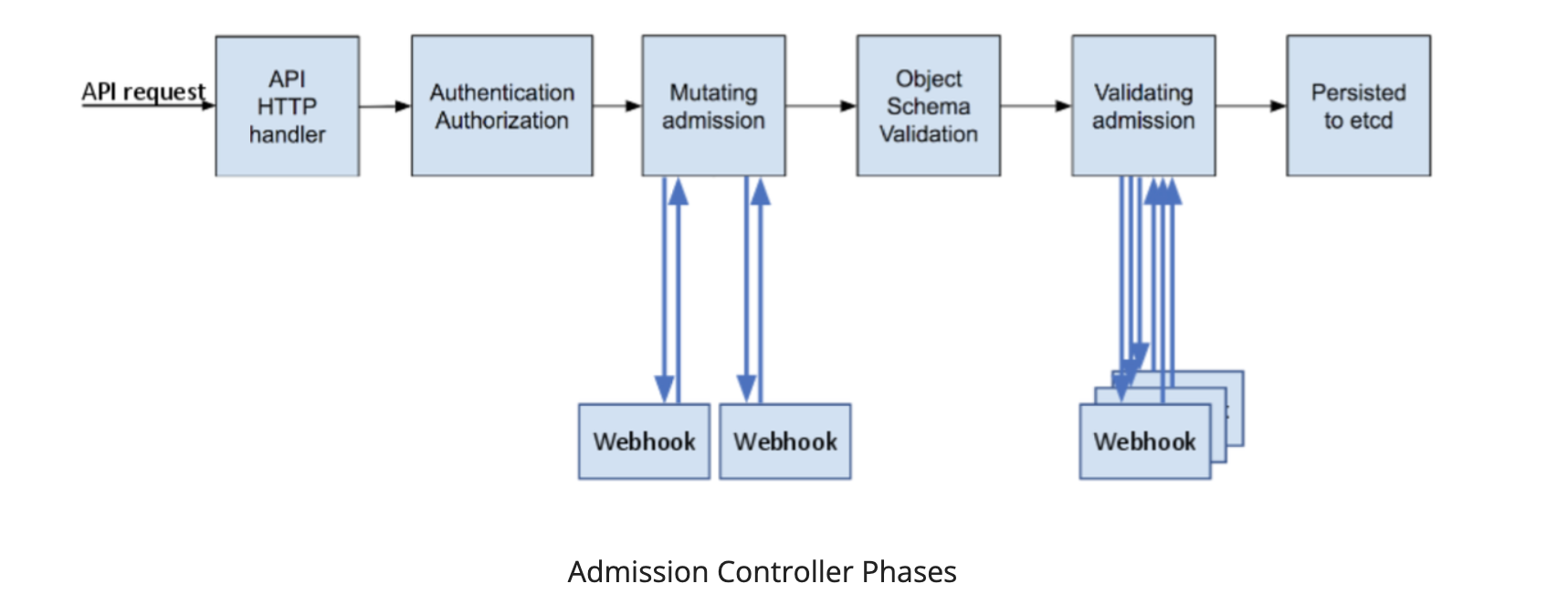
Webhook configurations are executed during the process of intercepting authenticated API request to accept an object request or deny an object by Kubernetes Admission controllers. Kubernetes admission controllers sets a security baseline across namespace or cluster. The following diagram decribes the different steps involved in the admission controller process.
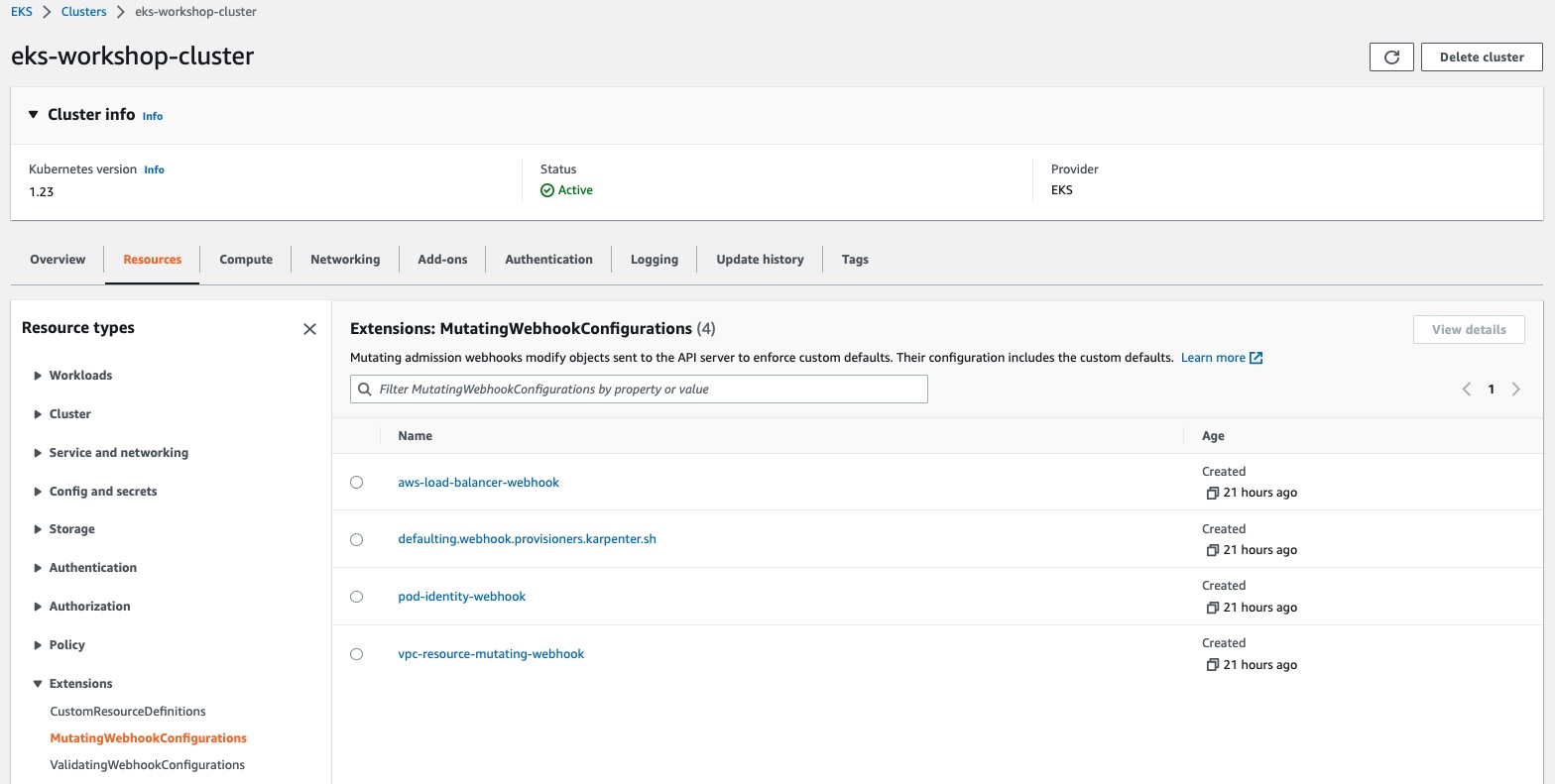
Mutating admission webhooks modify objects sent to the API server to enforce custom defaults.
Under Resource Types - Extensions you can view a list of the Mutating Webhook Configurations on the cluster
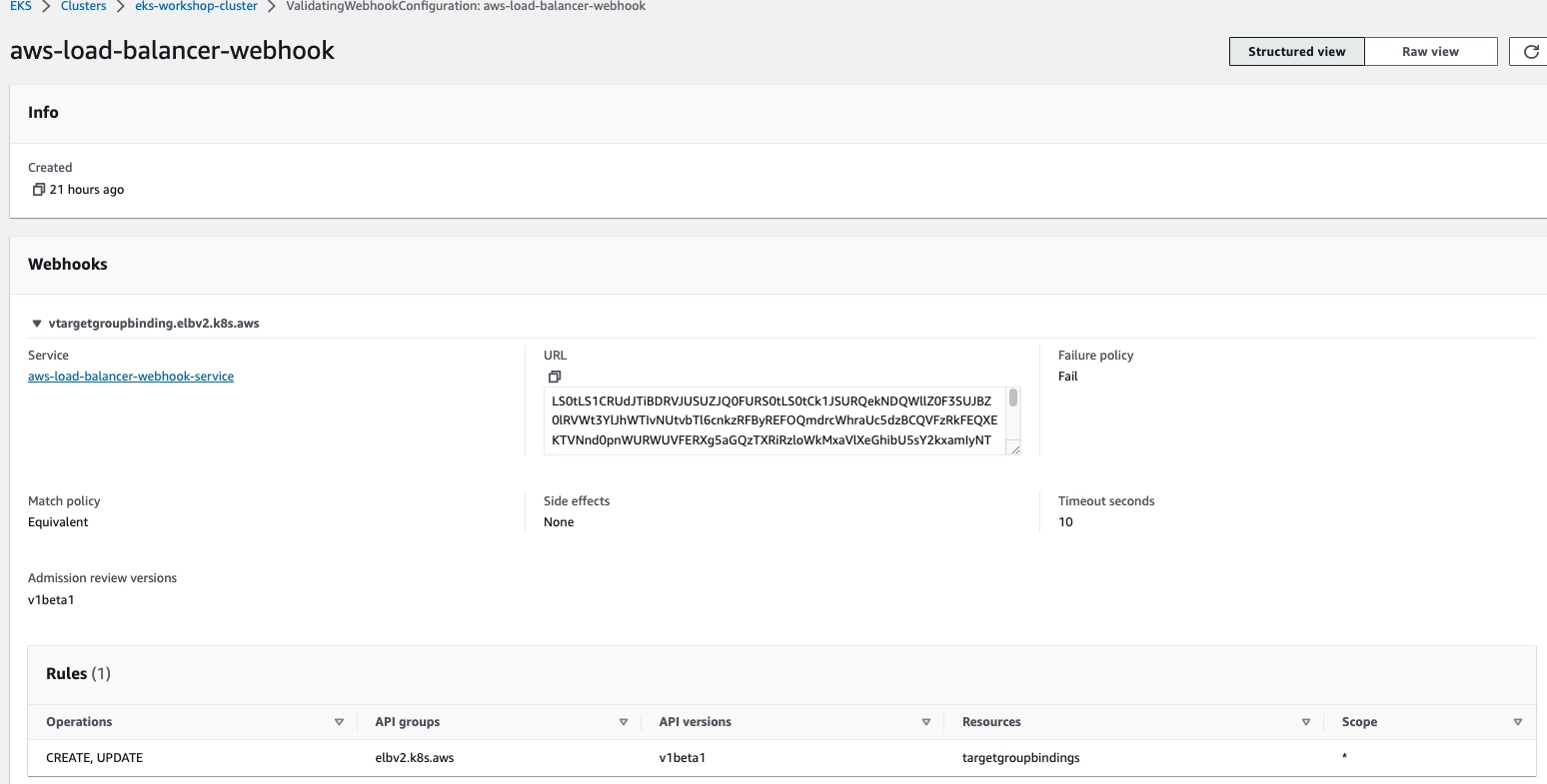
The below screenshot shows the details of the aws-load-balancer-webhook. You can see in this webhook configuration that Match policy = Equivalent which means
request will be sent to webhook by modifying the object as per the webhook version Admission review version = v1beta1.
When the configuration Match policy = Equivalent then when a new request is processed but has a different webhook version then specified in the configuration, the request will not be sent to webhook. Notice the Side Effects is set to None and the Timeout Seconds is set to 10 meaning this webhook has no side effects and will be rejected after 10 seconds.
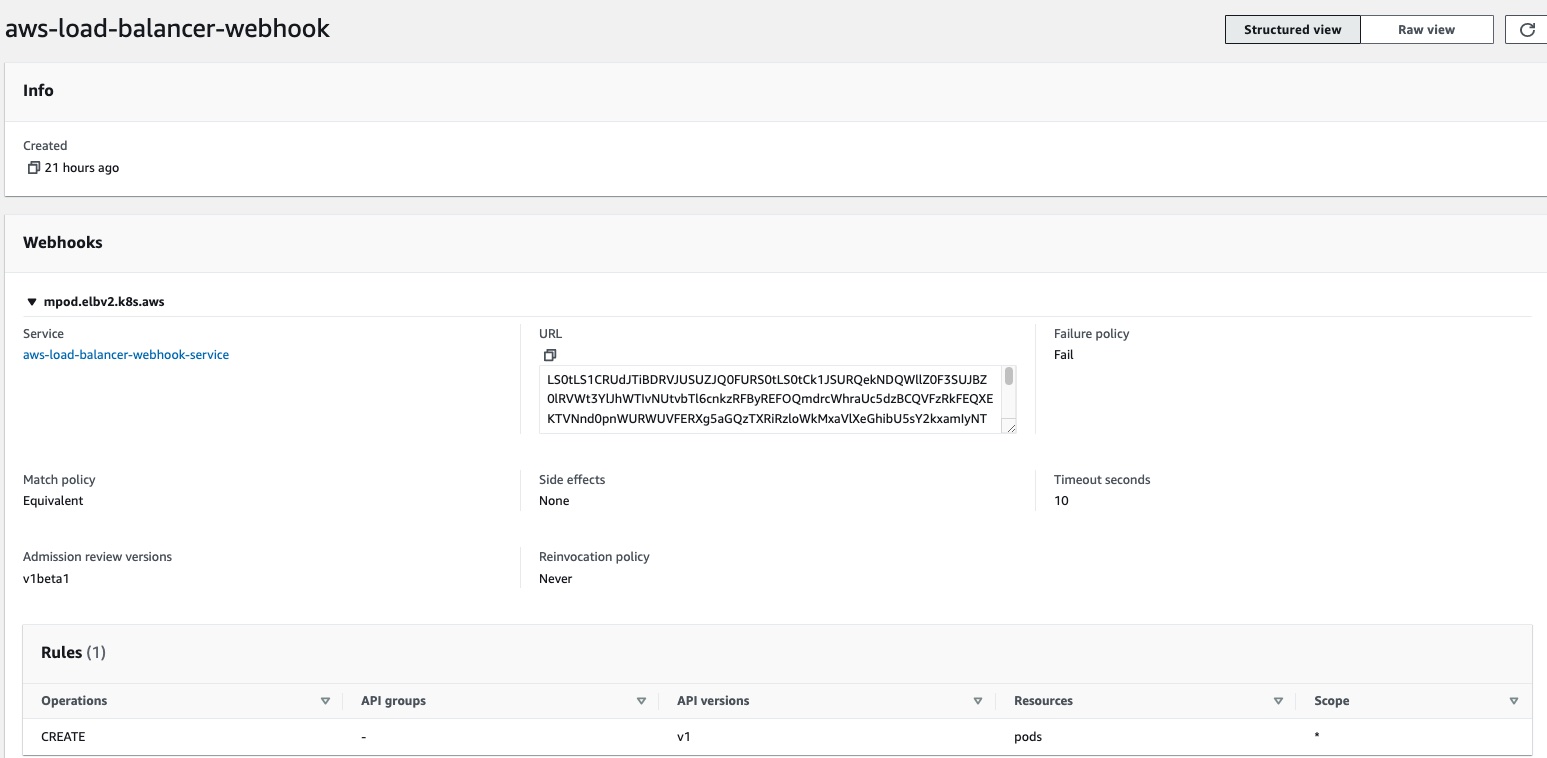
Validating admission webhooks validate requests to the API server. Their configuration includes settings to validate requests. Configurations of ValidatingAdmissionWebhooks are similar to MutatingAdmissionWebhook, however the final status of ValidatingAdmissionWebhooks request objects are stored in etcd.