Provisioning ACK resources
By default, the Carts component in the sample application uses a DynamoDB local instance running as a pod in the EKS cluster called carts-dynamodb. In this section of the lab, we'll provision an Amazon DynamoDB cloud-based table for our application using Kubernetes custom resources and configure the Carts deployment to use this newly provisioned DynamoDB table instead of the local copy.
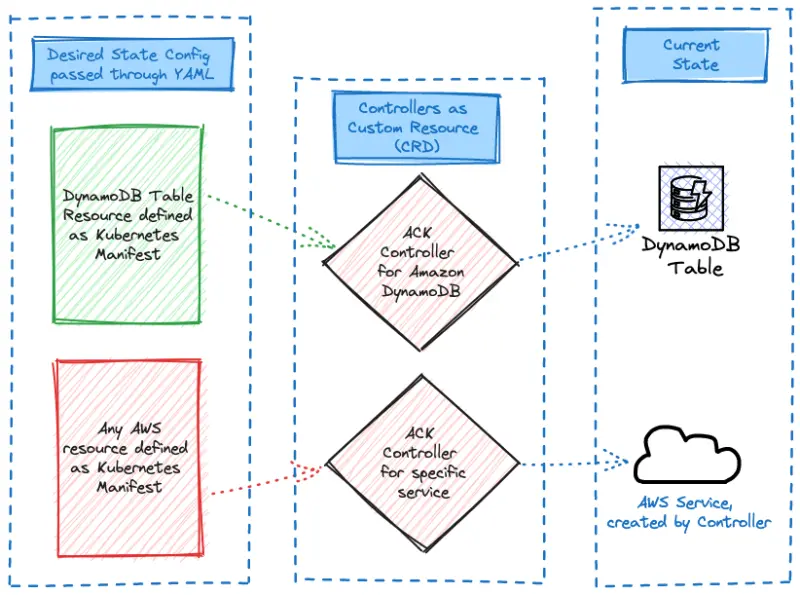
Let's examine how we can create the DynamoDB Table using a Kubernetes manifest:
apiVersion: dynamodb.services.k8s.aws/v1alpha1
kind: Table
metadata:
name: items
namespace: carts
spec:
keySchema:
- attributeName: id
keyType: HASH
attributeDefinitions:
- attributeName: id
attributeType: "S"
- attributeName: customerId
attributeType: "S"
billingMode: PAY_PER_REQUEST
tableName: "${EKS_CLUSTER_NAME}-carts-ack"
globalSecondaryIndexes:
- indexName: idx_global_customerId
keySchema:
- attributeName: customerId
keyType: HASH
- attributeName: id
keyType: RANGE
projection:
projectionType: "ALL"
Uses ACK DynamoDB controller
Creates a DynamoDB table resource
Specify Primary key using id attribute as partition key (HASH)
Defines id and customerId as string attributes
Specifies On-demand pricing model
Specifies the DynamoDB table name using the ${EKS_CLUSTER_NAME} environment variable prefix
Creates a global secondary index named idx_global_customerId that enables efficient queries by customerID with all table attributes projected
Keen observers will notice that the YAML specification closely resembles the API signature for DynamoDB, including familiar fields such as tableName and attributeDefinitions.
Now, let's apply these updates to the cluster:
table.dynamodb.services.k8s.aws/items created
The ACK controllers in the cluster will respond to these new resources and provision the AWS infrastructure we've defined in the manifests. To verify that ACK has created the table, run the following command:
table.dynamodb.services.k8s.aws/items condition met
ACTIVE
Finally, let's confirm that the table has been created using the AWS CLI:
{"TableNames": [
"eks-workshop-carts-ack"
]
}
This output confirms that our new table has been successfully created!
By leveraging ACK, we've seamlessly provisioned a cloud-based DynamoDB table directly from our Kubernetes cluster, demonstrating the power and flexibility of this approach to managing AWS resources.